Blog

Technology
Best Free AI Tools to Remove Backgrounds and Create Transparent PNGs (2026 Comparison)
Out there among online stores and posts on social apps, sharp pictures matter more than ever. When it’s time to...

Technology
Essential Reasons To Switch From Passwords To Passkeys Today
The digital security world is presently experiencing the most radical change since the internet was invented. The “shared secret”—the password—has...
Technology
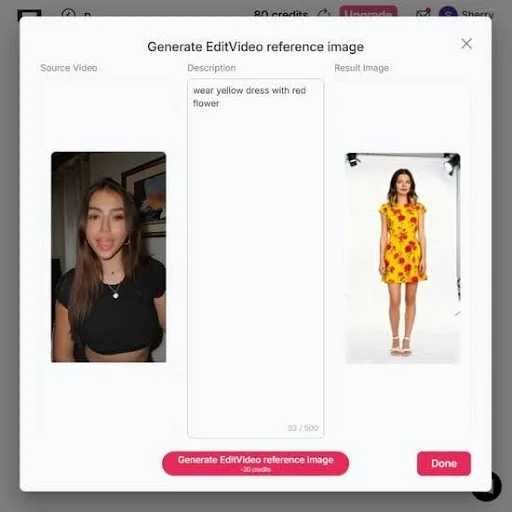
Seedance 1.5 is the Tech, but APOB AI is the Strategy: How Creators are Actually Winning in 2026
If you’ve been scrolling through AI video forums lately, you’ve probably seen the hype around Seedance 1.5. It’s the latest...

Technology
Exploring Oscilloscopes: A Complete Guide to Electronic Signal Measurement and Waveform Analysis
Discover everything you need to know about oscilloscopes, including digital and mixed-signal types, waveform analysis, signal measurement, and essential features...

Technology
How GPS Trackers and Dash Cams With GPS Are Revolutionizing Fleet Management
Fleet management has evolved dramatically over the past decade, driven by technological advancements that allow companies to optimize operations, improve...

Technology
езиково значение: The Psychology Behind Human Communication
Introduction to езиково значение Communication is the lifeblood of human interaction. It’s how we express our thoughts, share our feelings,...

Technology
Qiser: Unlocking Next-Level Efficiency Across Tech, Health, and Finance
Introduction to Qiser In today’s fast-paced world, efficiency is more than just a buzzword; it’s the key to thriving in...

Technology
Bynethi com: Bridging Technology, Travel, Health, and Lifestyle in One Place
Introduction to Bynethi com Welcome to the world of Bynethi com, where innovation meets everyday living. Imagine a platform that...
Technology
From Friction to Film: Sora 2, Veo 3, and Wan 2.5 – Choosing the Best AI Video Model for Your Vision
The blank canvas has always been a site of silent struggle. For creators, the initial spark of an idea is...

Technology
The Invisible Web: How Algorithms Decide What You See
In the early days of the internet, the web was primarily a collection of static pages accessed through directories or...





